Hackers Infecting Apple App Developers With Trojanized Xcode Projects
Cybersecurity researchers on Thursday disclosed a new attack wherein threat actors are leveraging Xcode as an attack vector to compromise Apple platform developers with a backdoor, adding to a growing trend that involves targeting developers and researchers with malicious attacks.
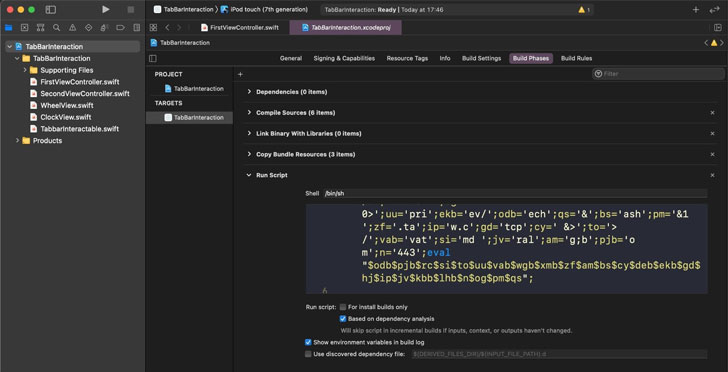
Dubbed "XcodeSpy," the trojanized Xcode project is a tainted version of a legitimate, open-source project available on GitHub called TabBarInteraction that's used by developers to animate iOS tab bars based on user interaction.
"XcodeSpy is a malicious Xcode project that installs a custom variant of the EggShell backdoor on the developer's macOS computer along with a persistence mechanism," SentinelOne researchers said.
Xcode is Apple's integrated development environment (IDE) for macOS, used to develop software for macOS, iOS, iPadOS, watchOS, and tvOS.
Earlier this year, Google's Threat Analysis group uncovered a North Korean campaign aimed at security researchers and exploit developers, which entailed the sharing of a Visual Studio project designed to load a malicious DLL on Windows systems.
The doctored Xcode project does something similar, only this time the attacks have singled out Apple developers.
Besides including the original code, XcodeSpy also contains an obfuscated Run Script that's executed when the developer's build target is launched. The script then contacts an attacker-controlled server to retrieve a custom variant of the EggShell backdoor on the development machine, which comes with capabilities to record information from the victim's microphone, camera, and keyboard.
"XcodeSpy takes advantage of a built-in feature of Apple's IDE which allows developers to run a custom shell script on launching an instance of their target application," the researchers said. "While the technique is easy to identify if looked for, new or inexperienced developers who are not aware of the Run Script feature are particularly at risk since there is no indication in the console or debugger to indicate execution of the malicious script."
SentinelOne said it identified two variants of the EggShell payload, with the samples uploaded to VirusTotal from Japan on August 5 and October 13 last year. Additional clues point to one unnamed U.S. organization that's said to have been targeted using this campaign between July and October 2020, with other developers in Asia likely to be targeted as well.
Adversaries have previously resorted to tainted Xcode executables (aka XCodeGhost) to inject malicious code into iOS apps compiled with the infected Xcode without the developers' knowledge, and subsequently use the infected apps to collect information from the devices once they are downloaded and installed from the App Store.
Then in August 2020, researchers from Trend Micro unearth a similar threat that spread via modified Xcode projects, which, upon building, were configured to install a mac malware called XCSSET to steal credentials, capture screenshots, sensitive data from messaging and note taking apps, and even encrypt files for a ransom.
But XcodeSpy, in contrast, takes an easier route, since the goal appears to be to strike the developers themselves, although the ultimate objective behind the exploitation and the identity of the group behind it remains unclear as yet.
"Targeting software developers is the first step in a successful supply chain attack. One way to do so is to abuse the very development tools necessary to carry out this work," the researchers said.
"It is entirely possible that XcodeSpy may have been targeted at a particular developer or group of developers, but there are other potential scenarios with such high-value victims. Attackers could simply be trawling for interesting targets and gathering data for future campaigns, or they could be attempting to gather AppleID credentials for use in other campaigns that use malware with valid Apple Developer code signatures."

Comments